Terraform for deploying an Azure landing zone for NC2
Introduction
This guide introduces a Terraform / OpenTofu module designed to automate the creation of all Azure resources required to successfully deploy a Nutanix Cloud Clusters (NC2) environment on Azure. It also extends to adding an Azure Route Server and a Site-2-site VPN configuration with BGP routing.
Basically, it deploys everything needed to run NC2 but not the NC2 cluster itself. The cluster is deployed through the NC2 portal or via the API. So, if you run this you will end up with an Azure resource group containing everything NC2 needs to function correctly as well as connectivity via S2S VPN to an on-prem lab or datacenter.
Benefits of automation
Automation with Terraform and OpenTofu brings several significant advantages:
- Time Efficiency: Manual configuration of NC2 environments can be time-consuming. These scripts automate the process, reducing deployment time from hours to minutes.
- Reduce human error: Creating an Azure environment which checks all the boxes for what NC2 needs can be complex and error prone if done manually.
- Consistency: Automated deployments ensure consistent configurations across different environments.
- Reproducibility: The infrastructure can be easily recreated or modified using the same code.
- Version Control: Infrastructure changes can be tracked and managed through version control systems.
Features of the Terraform module
The deployment creates the following resources:
- Hub Virtual Network (HUB) with subnets
- Flow Gateway (FGW) Virtual Network
- Cluster (CLSTR) Virtual Network
- Prism Central (PC) Virtual Network
- VNet peering between all networks (mesh - required for NC2)
- VPN Gateway with BGP support
- NAT Gateways for outbound connectivity in each VNet
- Azure Route Server for BGP routing
- Additional required settings for NC2, like DNS, fastpath tagging, etc.
Networking
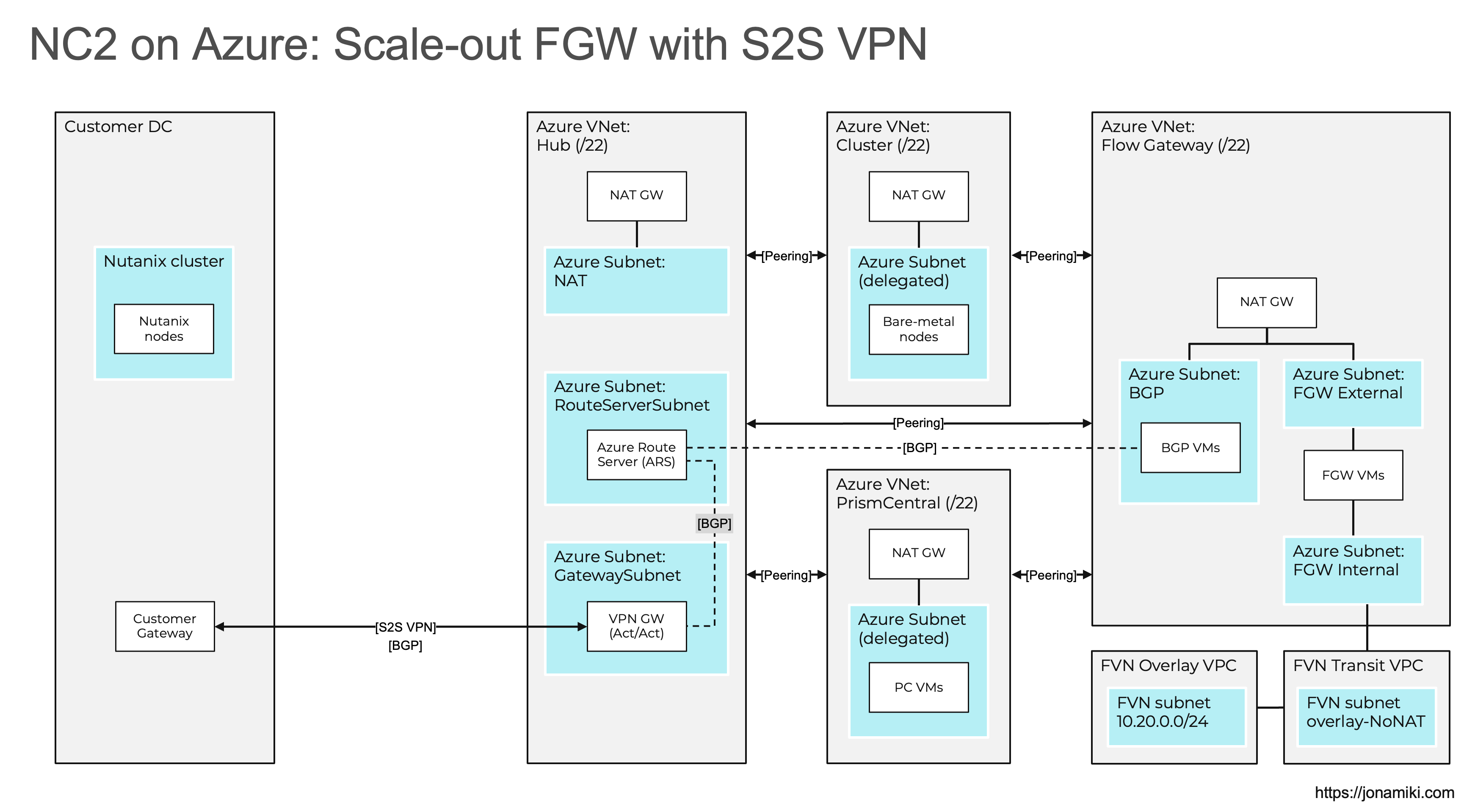
When applied, the module will create an environment designed to support a scale-out Flow Gateway model supporting BGP for routing of overlay networks. This is beneficial for automatically sharing routes from any subnets created as overlay networks on NC2. These can be advertised via the Azure Route Server to the rest of the Azure environment as well as via a S2S VPN or ExpressRoute to an on-prem DC or office.
Solution architecture diagram
The components shown in the below diagram will be deployed, minus the NC2 environment and of course the on-premises DC.
Note
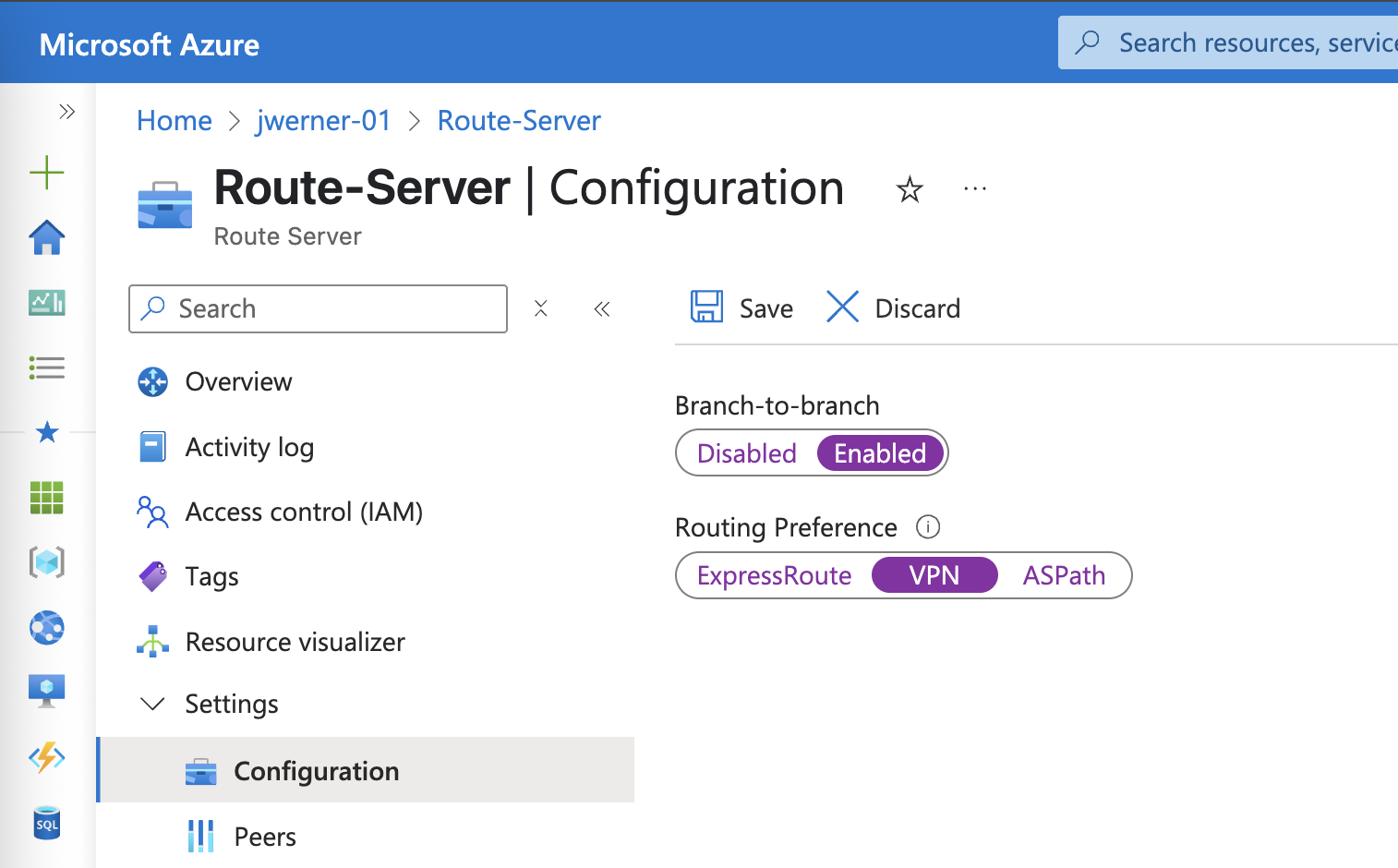
Post deployment, navigate to: Route Server -> Settings -> Configuration and update the “Branch-to-branch” setting to “Enabled”. This is required for the Route Server to share NC2 overlay network routes over BGP. Also change the “Routing Preference” to “VPN” to ensure the RS shares the routes with the VPN GW instance.
Download
The samples can be downloaded / cloned from the following GitHub repository: https://github.com/jonas-werner/nc2-on-azure-landing-zone
1
git clone https://github.com/jonas-werner/nc2-on-azure-landing-zone.git
Conclusion
This guide has given an introduction to a Terraform module for deploying an Azure landing zone in preparation for an NC2 deployment on Azure. Hopefully it has been useful. Please refer to the links below for more resources.