Problem statement
For infrequent VPN connectivity between on-prem labs / data centers and AWS it doesn’t make sense to have a permanent VPN connection up 24/7. However, configuring the on-premises Mikrotik router each time is time consuming and error-prone when done manually.
Functionality
This Python script connects to AWS using boto3, reads the details for the first VPN connection it can find and then generates the commands required to set up:
- Inside IP addresses for the VPN tunnel
- IPsec proposal settings
- IPset profile settings
- IPsec peers
- IPsec secrets
- BGP peers
- BGP networks to advertise
- Firewall setting
- etc.
After the commands are generated, simply copy and paste into a Mikrotik CLI window over SSH or similar and the connection will come up in a couple of minutes.
Prerequisites
This script only handles the on-prem side of the connectivity. It assumes the following is already in place at the AWS side:
- VPC with subnets
- CGW (Customer Gateway)
- VGW (Virtual Private Gateway) which is attached to the VPC
- VPN connection configured to use the VGW and CGW
If you require information on how to set up the AWS-side components, please refer to this blog post: https://jonamiki.com/2022/05/04/mikrotik-vpn-to-aws-vpc/
Script download
Please refer to this GitHub page for the script itself:
https://github.com/jonas-werner/aws-vpn-mikrotik-config-generator/tree/main
Example of running the script
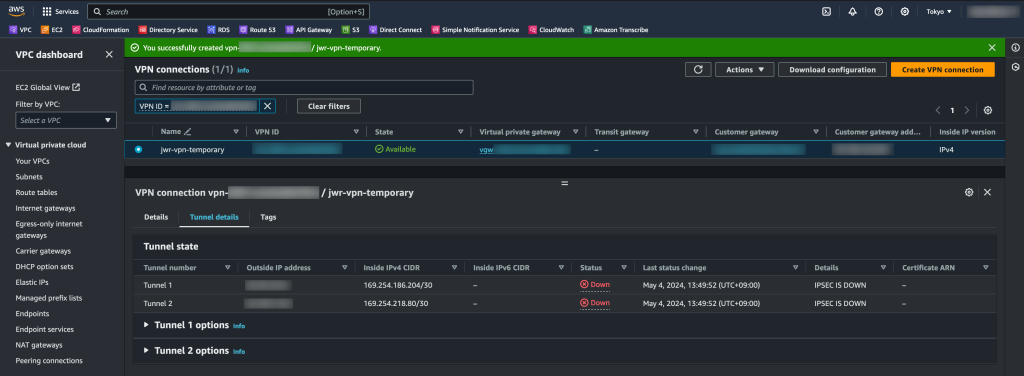
The AWS side has been configured but IPSEC and BGP are both down
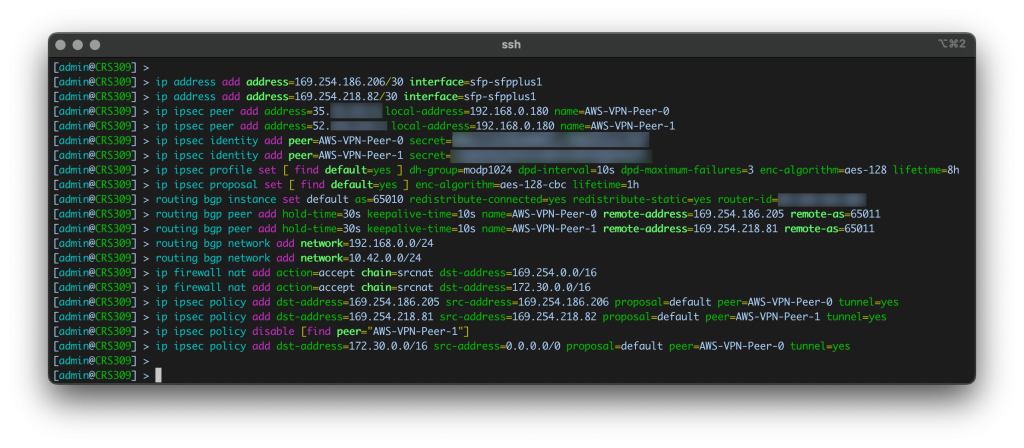
Running the script generates the commands required to connect the Mikrotik to AWS

Copy and paste the generated commands into the Mikrotik CLI
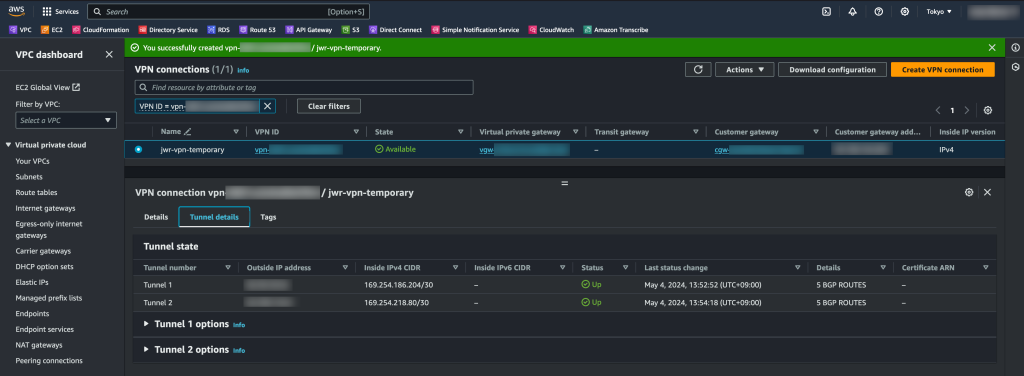
After a couple of minutes, IPSEC is up and routes are dynamically shared over BGP
More information
For more information, including how to set up the AWS VPN configuration and a more detailed explanation of the manual steps to configure the Mikrotik router, please refer to this blog post: https://jonamiki.com/2022/05/04/mikrotik-vpn-to-aws-vpc/

